BLOG | BY DWAYNE NATWICK
What is Defense in Depth?
When an organization is building a security program, they must consider the two primary threats, internal and external. Internal threats are from inside of the organization while external threats are bad actors that are attempting to access something from outside of the organization.
Improperly identifying and addressing internal and external threats can leave organizational data at risk. This can lead to data being exposed, compromised, and even lost, having negative effects on the organization both financially, and in the case of public companies, regulatory and reputational damage.
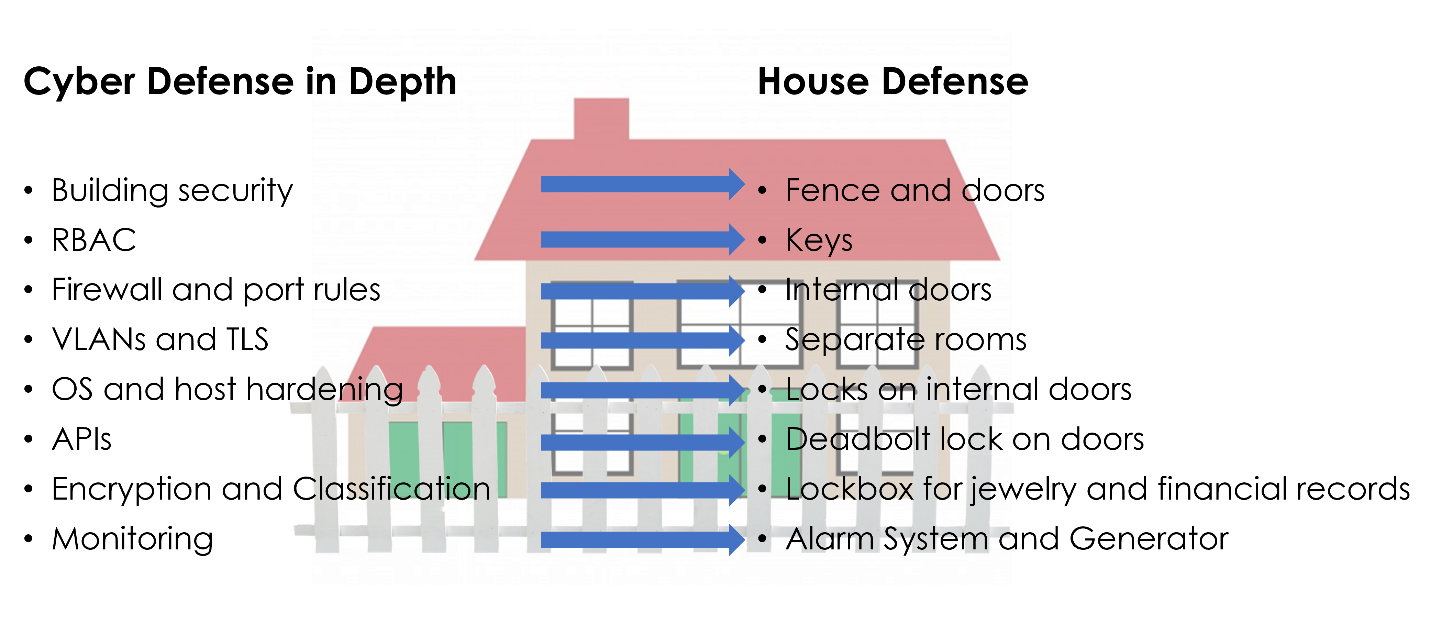
There are layers of protection to consider within a technology infrastructure. This is known as “defense in depth”. There are typically seven layers to build a security program and protect organizational data.
These layers each fulfill a purpose within our defense in depth strategy. Let’s look at each.
- Physical security which includes building security, such as exterior fences, concrete barriers, and doors. In an Azure or public cloud ecosystem, the cloud provider is responsible for this.
- Identity and Access is properly designing user, group, and resource access that makes sure that access provided is only to what is needed to get the job done.
- Perimeter security layer includes the firewall with port rules and access control lists that protects what transmits inbound and outbound.
- Network security builds upon the perimeter security by segmenting your network with multiple virtual networks.
- Compute security includes hardening of the host or hypervisor, which is the responsibility of the cloud provider in a public hosting scenario, and operating system hardening and building a secure virtual machine baseline.
- At the application layer, it is important to make sure that proper security is in place for APIs and that there are no developer “backdoors” left open before an application is put into production. If an application is accessing a database, that connection should be configured with proper roles and only allow internal connections.
- At the center of it all is the data, which is ultimately what we are trying to protect as an organization. The last line of defense here is to make sure that all data is encrypted at rest and in transit, that data is properly classified for role-based access, and that all encryption keys are protected and accessible when needed.
All these layers should be continuously monitored for best practices and effectiveness.
Why is defense in depth important?
Building a security program is like building a house. There are multiple layers of protection starting with a gated fence to protect the perimeter. Then the exterior doors with locks, and garage to protect your vehicles deter others from entering. Beyond the exterior, there may be multiple floors and interior doors with locks as a second line of defense. To monitor any potential threats, there could be an alarm system and a generator to maintain power to the home.
How does defense in depth relate to shared responsibility?
Shared responsibility within cloud environments is extremely important to understand. Shared responsibility provides the guidelines of where Microsoft Azure responsibility ends, and an organization's responsibility begins. This responsibility is different among the cloud delivery models.
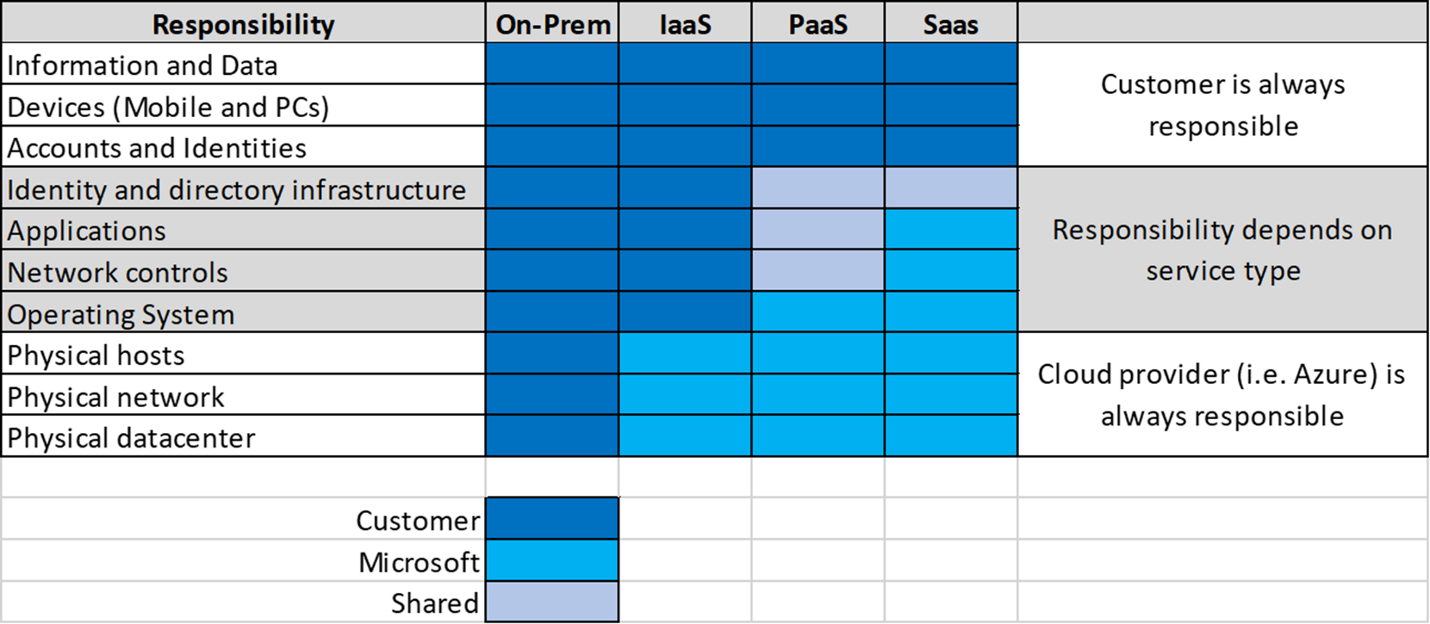
Looking at the graphic, organizational responsibility and infrastructure control are a direct correlation when moving from infrastructure, platform, or software as a service model.
Where do I start?
If you are new to the cloud, then planning is important. Having the right tools to monitor and audit your resources within the cloud is a good start. Microsoft Azure has several tools that can assist.
Azure Monitor is one of the most important services within Azure to monitor services. At the foundation of Azure Monitor is the agent that collects activity and diagnostic logs for services within Azure as well as outside resources.
Information from these agents are presented to the Monitor dashboard. Azure Monitor can be configured to receive network watcher information to determine connectivity issues within the environment.
Alerts can be created that set thresholds that may be a cause for concern with corresponding actions that identify what should be done if these alerts are triggered.
Azure Policy is a service that allows you to assign rules to govern the Azure subscription and resources.
Assigning a policy to a subscription or resource group enforces compliance when creating new resources. They will also audit existing resources against the policy for compliance and allow you to make the adjustments necessary to remediate those resources to comply.
Azure Policy feeds governance and compliance information into Azure Security Center. This information is gathered through assigned policies and initiatives within the subscription or resource groups.
Much of the data collected from the activity logs, service logs, and policies are fed into the Azure Security Center dashboard, such as MFA, updates, policy compliance, and RBAC roles. The security center dashboard can be used as a central source for policy and compliance of security controls.
Azure Security Center provides a central location for monitoring and managing your security posture.
Security Center provides a number of graphics and tools based on best practices that can assist you with:
- Review policy and compliance to regulatory controls
- Monitor resources to best practice security controls
- Review network topology and traffic for potential external threats
- Monitor and alert using advanced threat analysis and global threat intelligence maps
These tools can provide valuable insight into where your company stands in their defense in depth strategy. It will also provide recommendations for improving that strategy.
What next?
In the next post of this series, we are going to discuss zero trust as we protect the identity and access layer of our defense in depth security posture.
For more information on how to utilize Microsoft tools for security, compliance, and identity protection and governance, visit the Opsgility training calendar or contact us to schedule a consultation.

Dwayne Natwick - Azure MVP
Meet the author
Dwayne is a Microsoft Azure MVP and Cloud Training Architect Lead at Opsgility where I author content and provide live training. I am 18x certified in multiple Azure and M365 roles, including Microsoft 365 Fundamentals, Microsoft 365 Security Administrator Associate, Azure Solution Architect Expert, Azure Administrator Associate, and Azure Security Engineer Associate.
In addition to creating curriculum, training, and blog writing, I am also a Microsoft Certified Trainer and Regional Lead.