BLOG | BY KIT SKINNER
What is Azure AD?
Azure AD is based around Tenants utilized by organizations to hold security principals such as users and groups for universal identity and access management. These Tenants will each have their own unique, public DNS namespaces such as myazureaddomain.onmicrosoft.com as well as any custom DNS zones that you own that you would like to be utilized by Azure AD. However, each DNS name can only be used by one (1) Tenant, must be publicly routable (no .local's), and prove its managed by your organization (i.e. add unique records to validate).
You can then utilize these Tenants with services that integrate directly with Azure AD such as Azure Subscriptions, Microsoft 365, etc. or just about any public resource that supports industry standards such as OAuth or SAML.
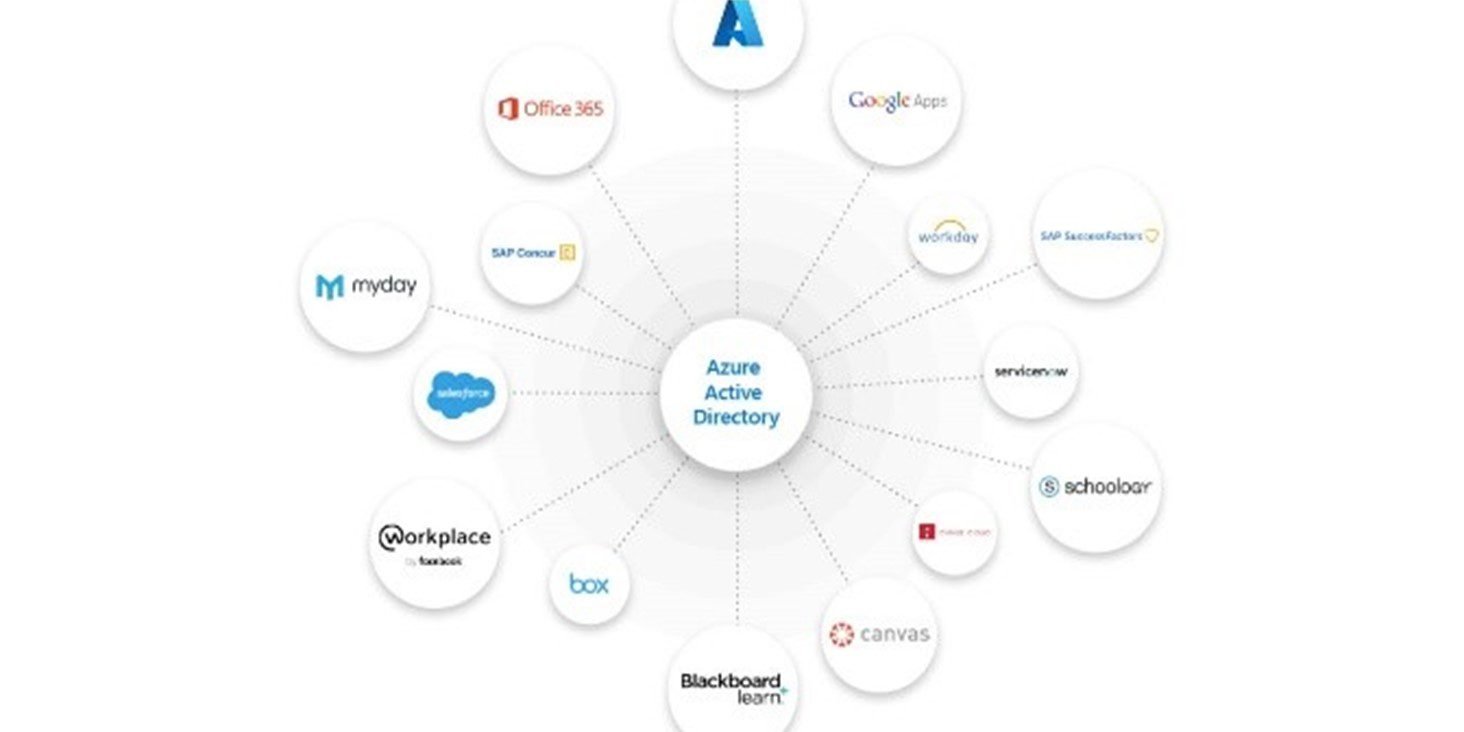
In addition, you can bring in users and other principals from other Tenants as guests to grant them access to resources that utilize your Tenant. By bringing the users over, you don't have to worry about supporting the users' basic logins, but can allow users to use their familiar logins they are used to.
What isn't Azure AD?
While Azure AD can replicate information from on premise via Azure AD Connect, Azure AD does not replace AD DS. Azure AD does not have integrated polices, organization trees (OUs), hierarchal tenant structures (i.e. forests), and legacy protocol support (i.e. Kerberos).
While newer devices can be joined or trusted via Azure AD, the management of the resources is not actually managed by Azure AD. However, other services such as Intune work with Azure AD and resources to take on those roles.
How can I optimize Azure AD?
By moving your organization to Azure AD, you gain a lot of features for security and monitoring of your authentication process. As you consolidate your user logins and experience by moving multiple applications to Azure AD, you can ensure your users' login process is more secure and monitored. This can allow you to bring in more features & more tools with Azure AD and use it on all your services.
With focusing on authentication controls and security options, Azure AD allows you to validate the user is who they say they are. You can then utilize the individual authorization tools with the different platforms being assured the users are authenticated.
Authentication Mechanism
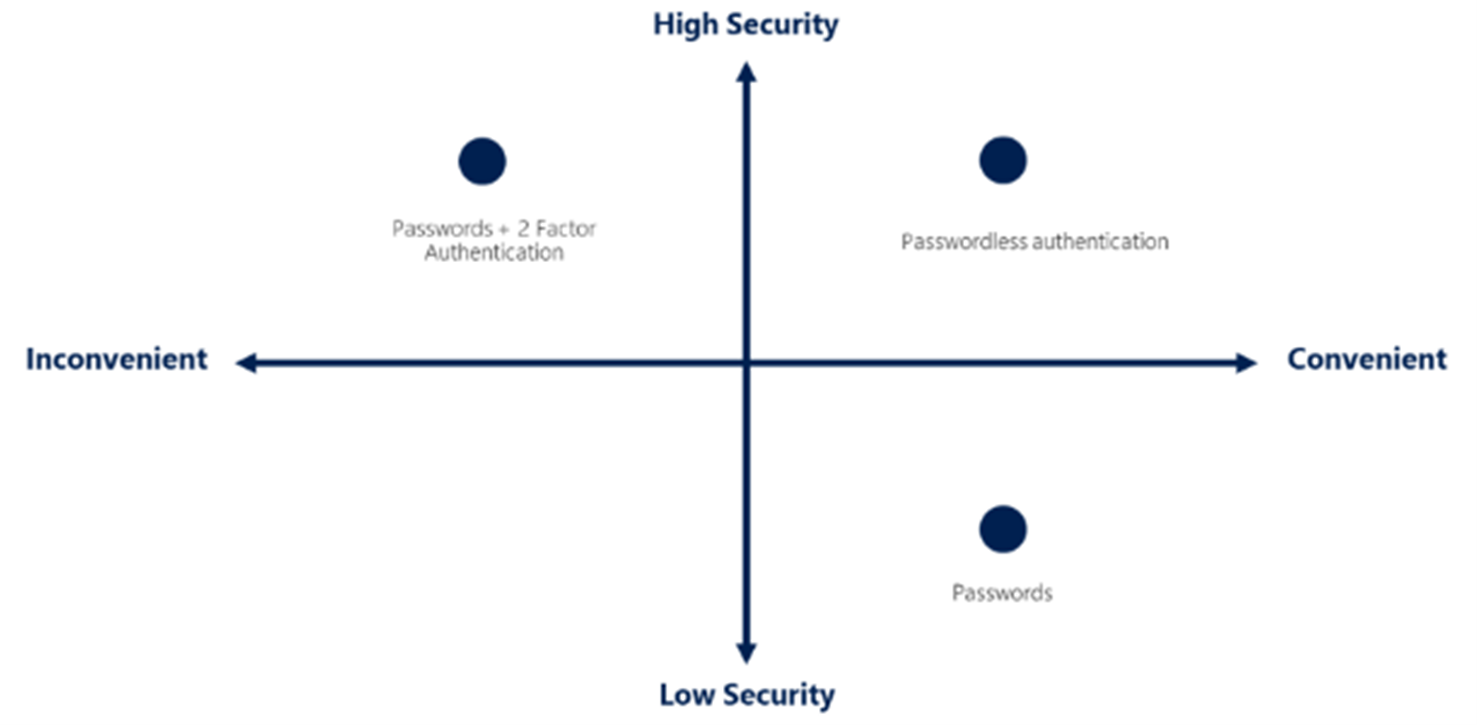
With centralized authentication of Azure AD, you can take advantage of different authentication mechanisms with Azure AD and allow any of your applications to utilize the advanced authentication without any additional configuration. For instance, enable multi-factor authentication (MFA) you can allow for a more secure login for all your current applications and new applications receive it immediately.
In addition, with the ease of passwordless authentication, we can allow the users to log in with secure device or biometric login, but not have them keep track of or remember a password. This feature then immediately becomes available to all your applications that would traditionally expect a password with its insecurities.
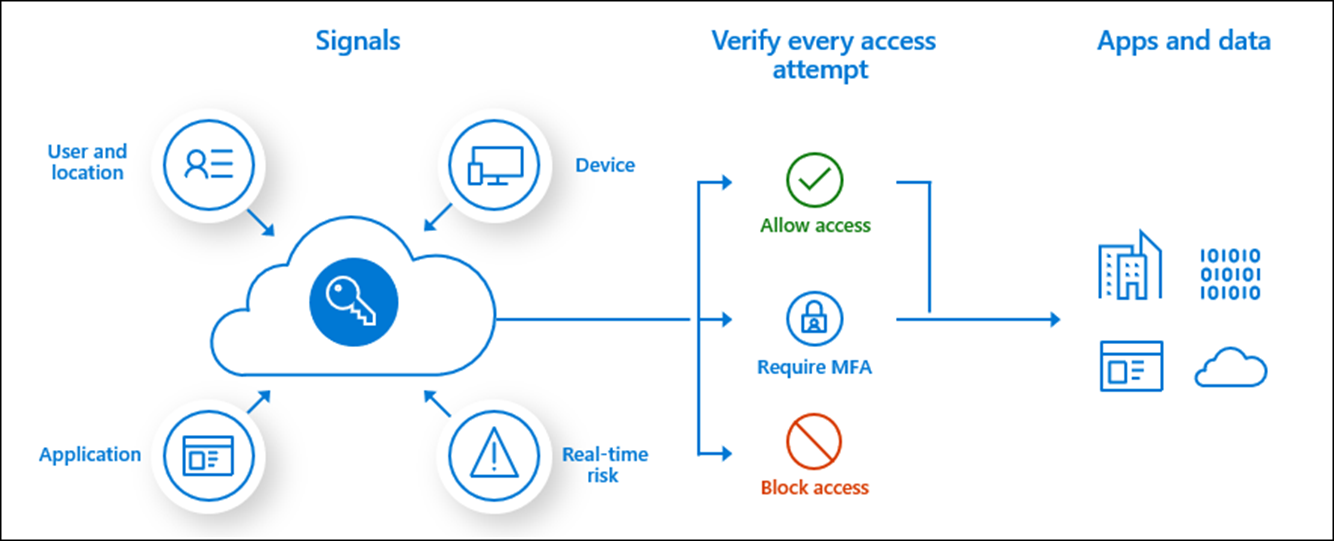
Conditional Policies
Azure AD also gives you the option of enabling Conditional Access by utilizing different parameters of the sign process (called signals), you can require certain conditions to be met before allowing the authentication process to complete. This can include things such as location, authentication method (ie: MFA), the risk of the sign (unlikely movement, suspicious IP), or what device their logging in with as well as what application they're attempting to access before you determine if the authentication will allow or block access to the application. This can all be done regardless of what the backend application is.
When can I use these?
All of these features are available for an Azure AD Tenant today, but some features such as Conditional Access require a premium license (P1 or P2) to utilize them. Some of these licenses are included in other packages such as Microsoft 365 E5 but can also be purchased independently if you are not utilizing other Microsoft services.

Kit Skinner - Cloud Architect Lead
Meet the author
Kit is responsible for delivering instructor-led training and creating on-demand & hands-on training. In addition, I am Infrastructure/Security SME for Microsoft Azure & Microsoft 365.
Prior to joining Opsgility, I have spent over 6 years Azure cloud consulting for various industries including manufacturing, distribution, healthcare, and government sectors and over 15 years in direct IT roles designing, running, and managing infrastructure & security.
Kit has over 20 years' experience in the IT industry, in roles spanning networking, infrastructure, technical pre-sales and system architecture.